This week, GLIMPS’ CTI team analyzed a new ransomware : Undergroud, spotten during their daily watch.
Static strain analysis.
0a08d9b027457da99725968eb4566eb836a7d503219ad5690f851caecabce93d
This file was analyzed by GLIMPS Malware as malicious. Thanks to this platform, we are able to effectively proceed to the analysis.
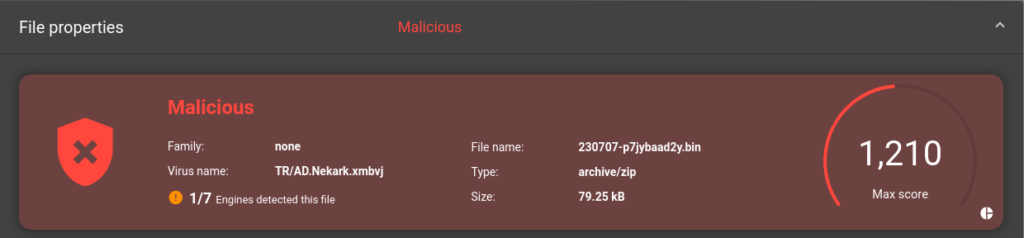
This ransomware family is not yet referenced into known data base, this led us to think that it is a new family ; furthermore, antivirus sotwares (signature analysis) are currently unware of it.
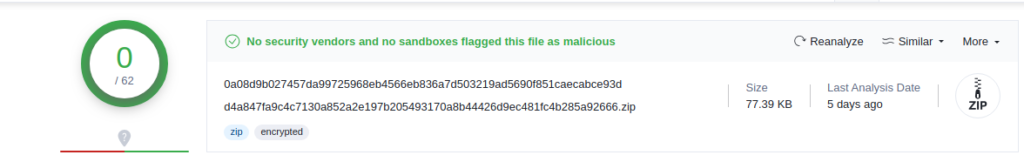
A study of the strings shows that a ransom note is indeed present called “%s!!readme!!!.txt”. “%s” being potentially a personalization variable which will be replaced by a victim identifier (victim name, random ID, etc…) when the ransomware is executed.
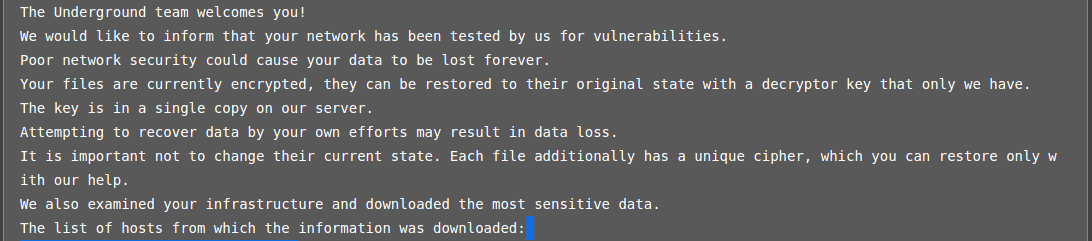
A TOR link appears enable you to contact the group using a login/password supplied in this same note.
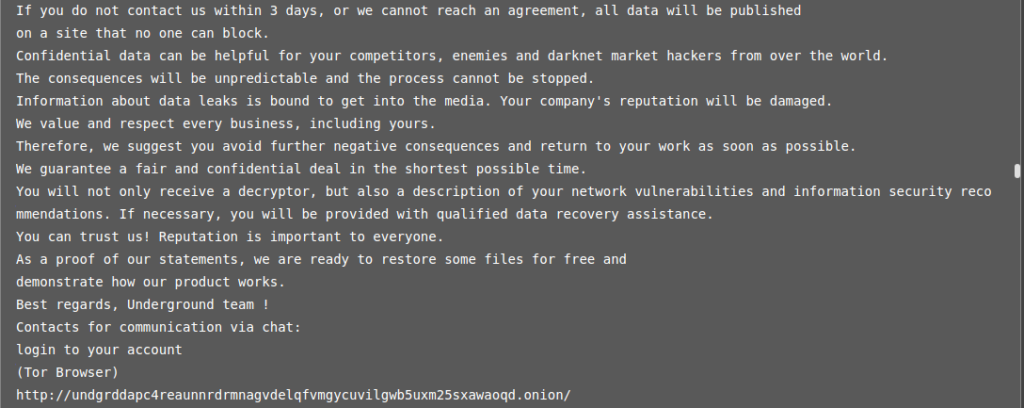
Conclusion
We know thanks to GLIMPS Malware analysis, that we are indeed facing a ransomware. The functions and ransom note leave no doubts as to the categorization of the file. Indicators contained in the ransom note inform us that the group is called Underground.
Appendices
| Hash | Description |
|---|---|
| 0a08d9b027457da99725968eb4566eb836a7d503219ad5690f851caecabce93d | Ransomware executable file |
| IOC | Description |
|---|---|
| %s!!readme!!!.txt | Ransom note |
| http://undgrddapc4reaunnrdrmnagvdelqfvmgycuvilgwb5uxm25sxawaoqd[.]onion | Ransom payment portal |
Sources
Do not hesitate to contact us for more information: contact@glimps.reA new #Ransomware is out named "Underground"!
— RAKESH KRISHNAN (@RakeshKrish12) July 10, 2023
Sample-
MD5: f60f0b756bda9b6aaff12c9768f0bc1ahttps://t.co/PiNiaaM8n1#OSINT #hack #security #infosec #malware #cybersecurity #cybersec #UndergroundRansomware #bitcoin #blockchain #darkweb #deepweb #cyberattack #TOR #CISA #FBI pic.twitter.com/rZlItWHeMX