Following the development of connectors with Sekoia, HarfangLab and Wallix, our partners in the OPEN XDR Platform, today is the time to highlight the integration between Vade and GLIMPS.
For those who haven’t been keeping up, we’ll start with a quick reminder of what the OPEN XDR Platform is:
The OPEN XDR Platform is a group of specialized, complementary cybersecurity software providers who have joined forces to create a platform offering tangible benefits. The platform is a feature-rich solution, capable of providing an immediate response to the ever-increasing number of cyberattacks.
Its modular, customizable and fully hybrid technology provides information to analysts and security managers for greater visibility and automation.
Who are the players on this platform?
While SEKOIA provides both its XDR Back-End and its Cyber Threat Intelligence platform, HarfangLab brings its EDR to detect and remediate threats on servers and workstations. The GLIMPS teams provide their code conceptualization technology and Extended Malware Analysis Platform for malware detection and analysis. Pradeo enriches the OPEN XDR Platform with its know-how in mobile security, and Vade with its expertise in email security. Gatewatcher brings its Aionig network threat detection and response solution. The latest addition is WALLIX, with its Privileged Access Management offering.
Vade X GLIMPS integration
Today, more than 90% of cyberattacks begin with a malicious email. The security of this flow is vital if companies want to protect themselves effectively against groups of attackers. To meet this challenge, Vade and GLIMPS have been working together to enable their customers and partners to benefit from their respective expertise.
A GLIMPS option is directly integrated into the “Vade for M365” interface, and will make it possible to respond to two specific use cases:
– Instantly raise doubts about files identified as suspicious or malicious
– Perform an in-depth analysis of malware received by e-mail
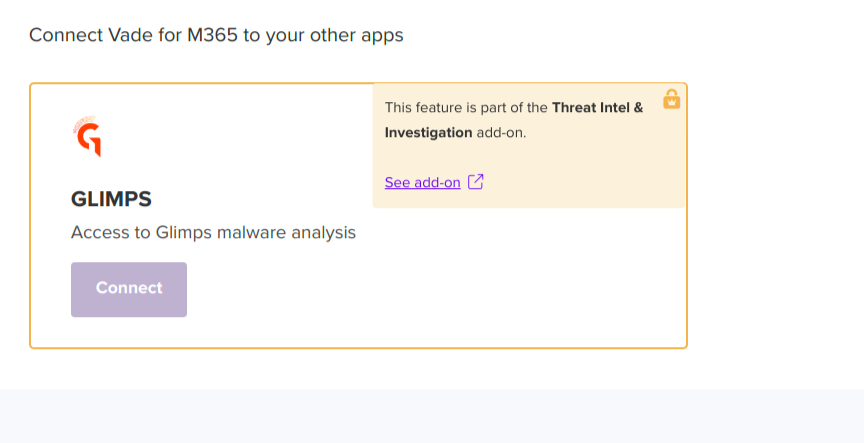
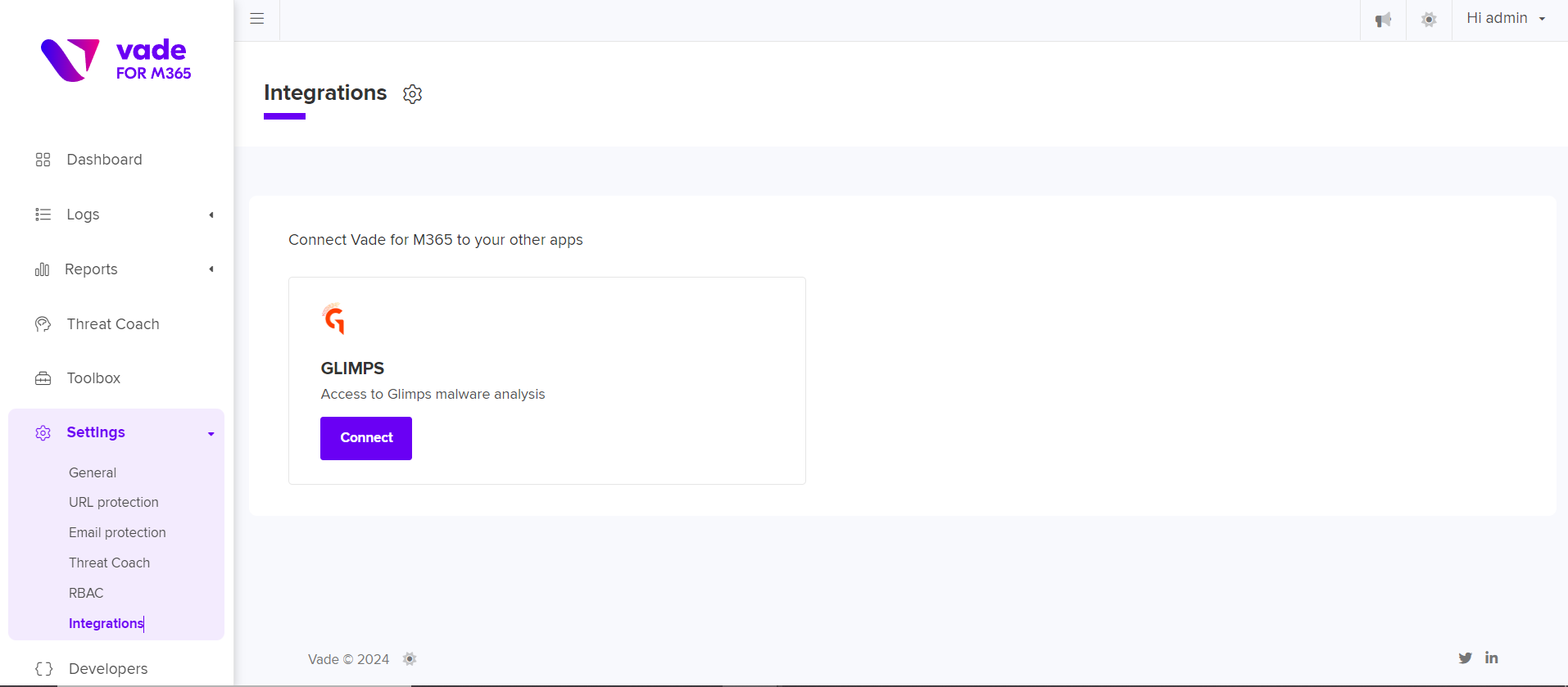
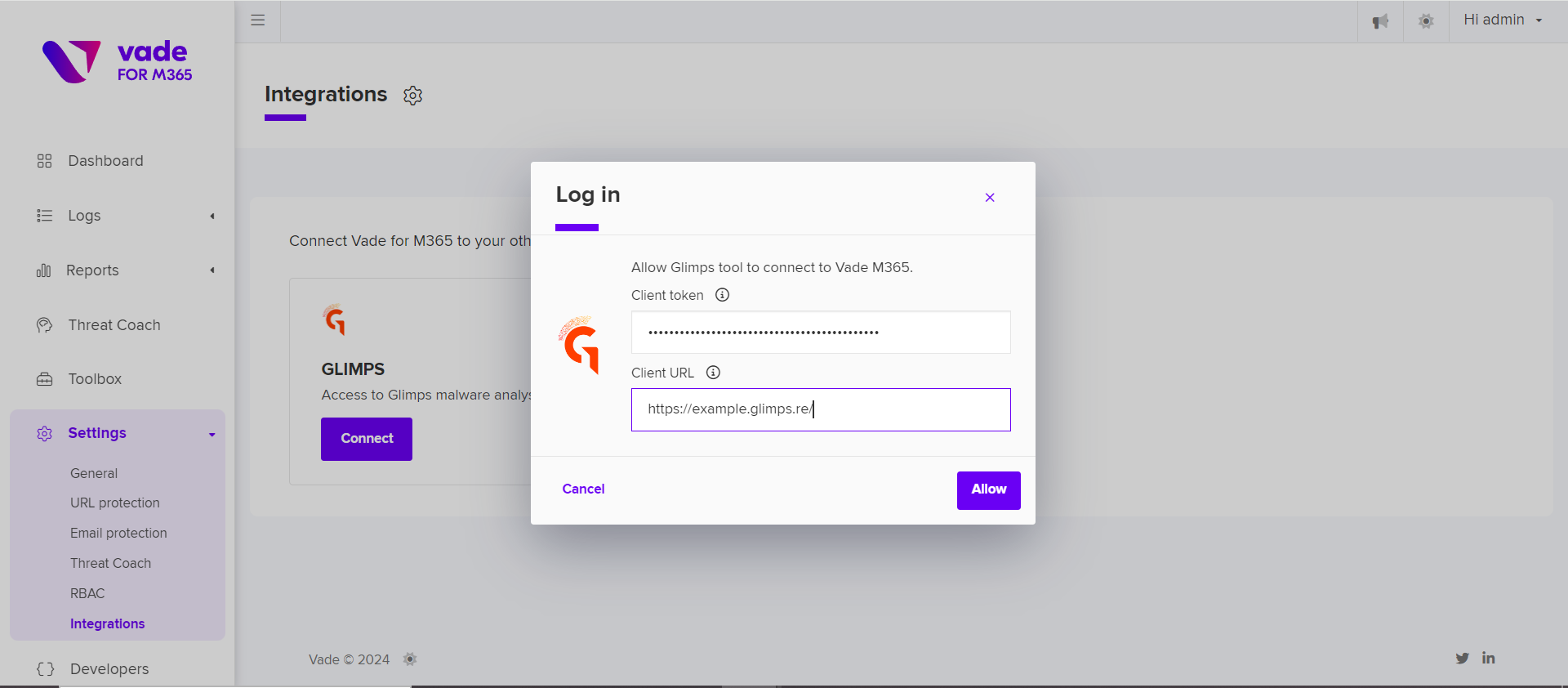
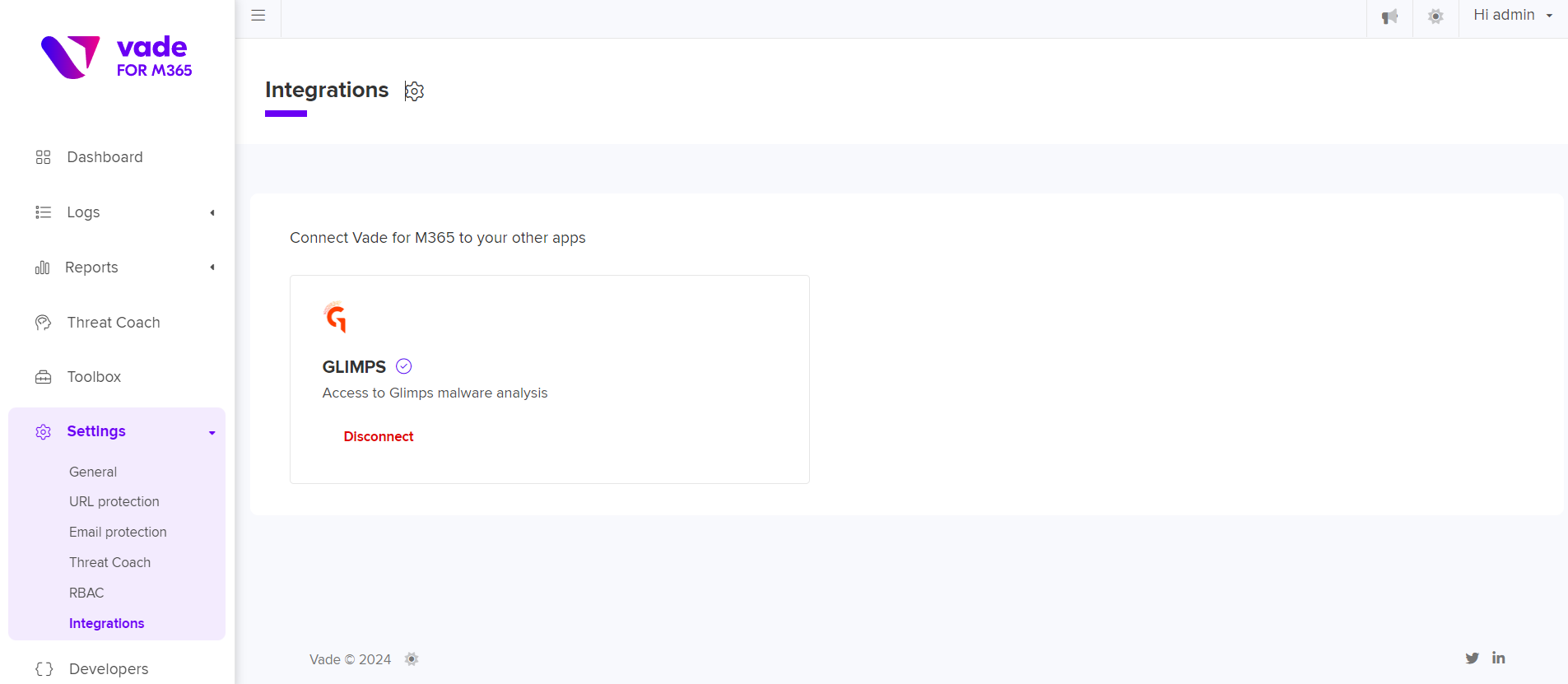
In the screenshots below, the attachments associated with this email identified as suspicious are extracted and can be sent for analysis to GLIMPS with a single click.
After a few seconds, an initial verdict is available, providing further information on the type of threat identified and its family. If the user requires further contextual information, he or she can switch directly to the GLIMPS Malware Expert interface via the “See full diagnostic” button.
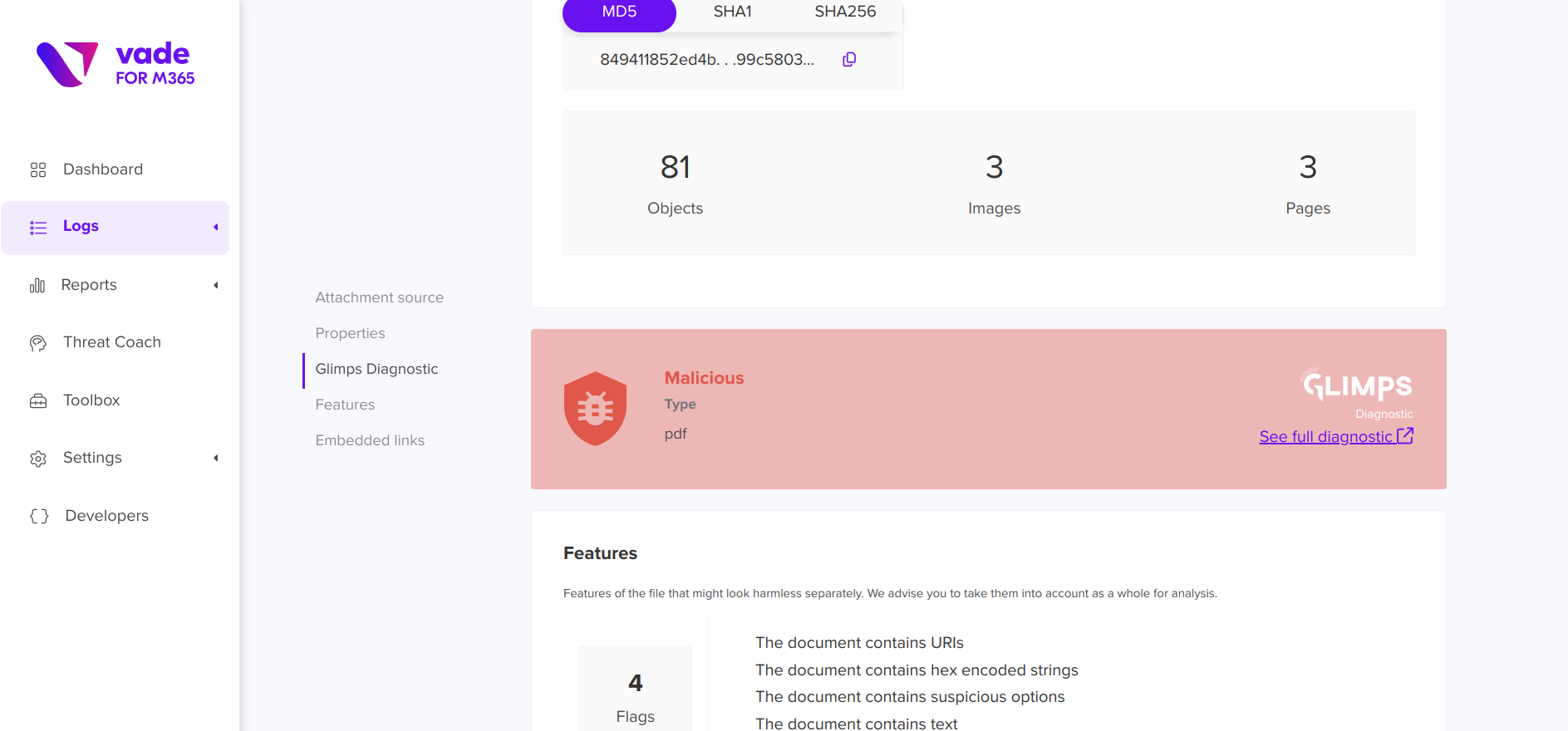
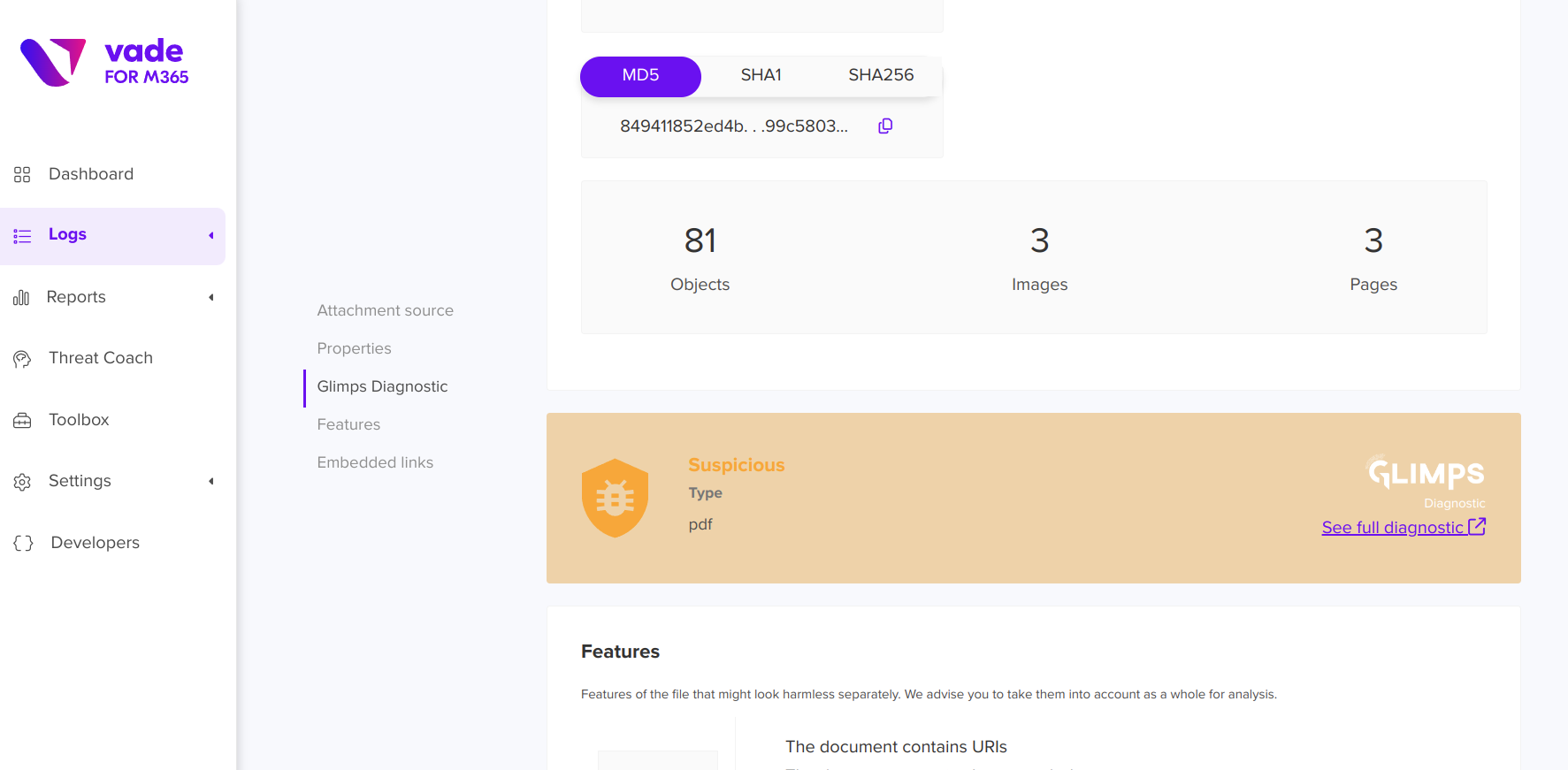
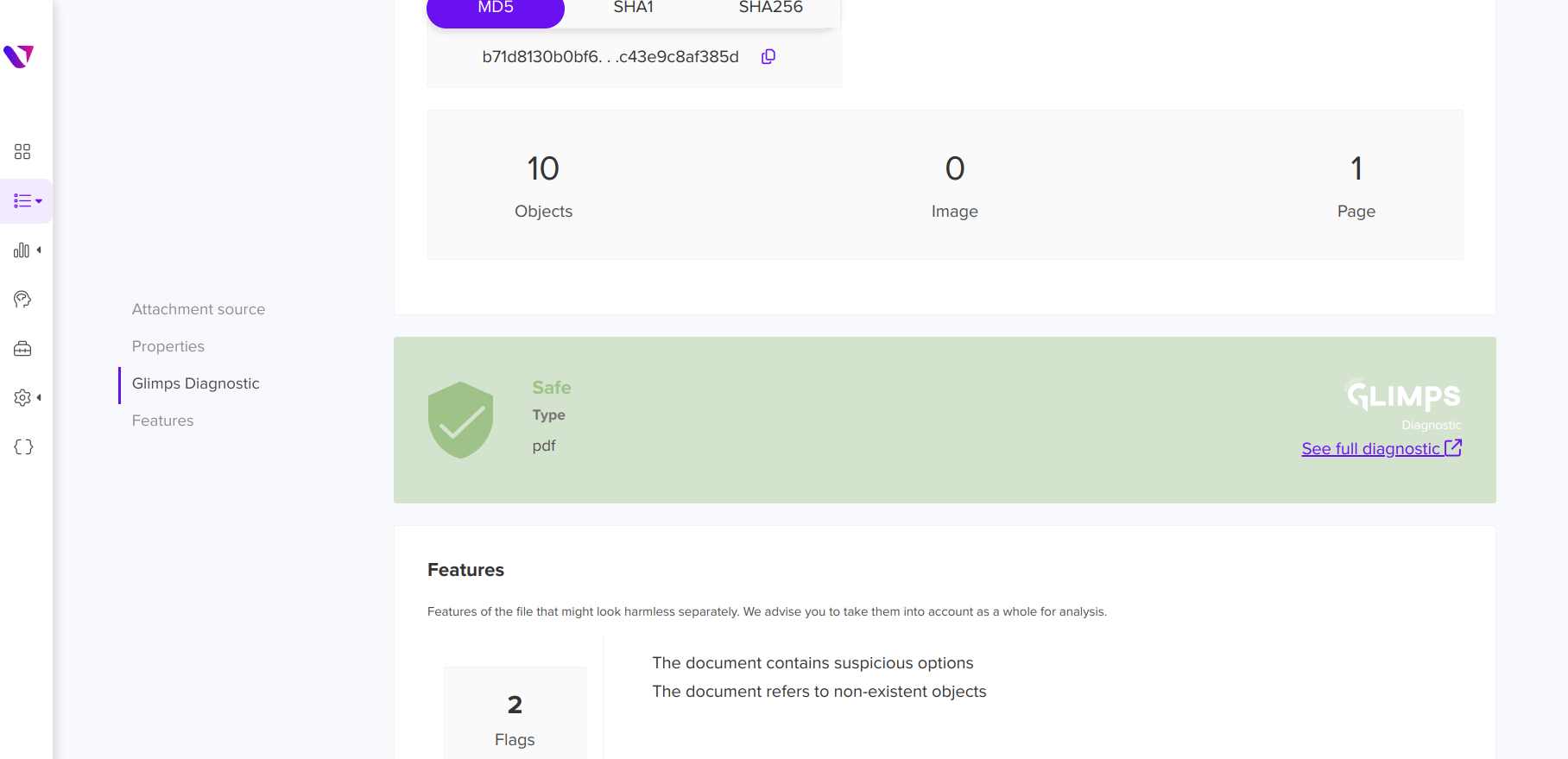
On GLIMPS’s interface, you’ll find a first level of Cyber Threat Intelligence, thanks to the integration of SEKOIA’s CTI feed relating to the malware identified by GLIMPS. You can even click on “View Full Report” to access the full report on the identified threat.
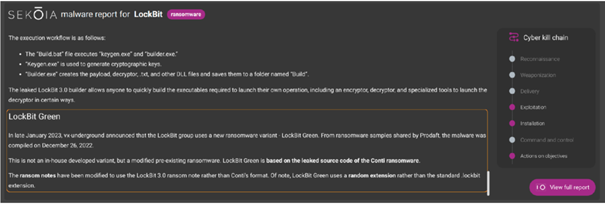
On the other hand, you can benefit from the power of GLIMPS’s unique AI engine, combined with over 30 modules and all the tools an analyst needs to sort out alerts and remove doubts.
For example, thanks to our visualization module, Office, PDF, Image and HTML files can be rendered harmlessly as images or secure documents, simply by clicking on the “File Preview” option – a significant time-saver that eliminates the need to handle suspect files and use virtualized environments.
What is the added value of this connector?
The integration of GLIMPS into Vade for M365 now offers an in-depth analysis option that complements Vade’s expertise in email protection.
The first level of characterization, available directly in the interface, will accelerate strategic decision-making thanks to an instant understanding of the threat.
If the user wishes to investigate further, it is possible to switch to the GLIMPS Malware expertise interface. By bringing together in a single environment all the tools used by analysts in their suspicion-finding and analysis operations, the solution reduces the “Mean Time to React” (MTTR) and increases the number of alerts processed daily by the teams.
Please contact us to find out more: contact@glimps.re