IDA is the industry-standard interactive disassembler and a powerful debugger. It is an essential binary code analysis tool with a broad spectrum of usage, including deep malware investigation, reverse engineering, and software analysis. GLIMPS provides a plugin for automatic feature identification. This plugin allows you to apply GLIMPS Audit analysis to the file sent to IDA Pro, allowing you to speed up the characterization.
In this post we will illustrate how to use these features introduced in IDA Pro.
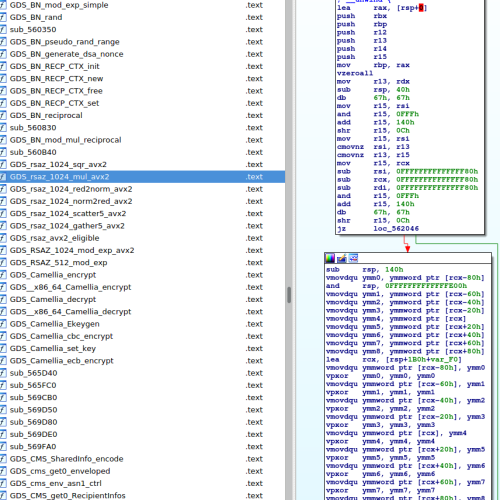
When you send a file to IDA, the software deconstructs the file to highlight its structure:
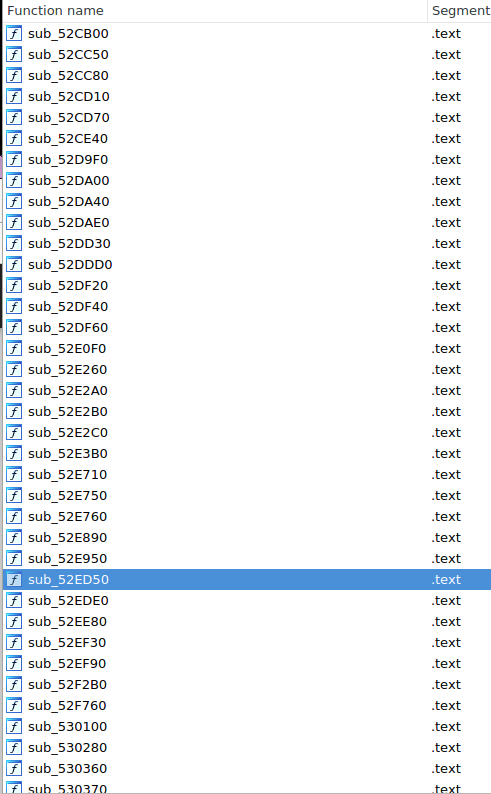
To know the symbols of all these functions, you just have to look for the plugin GLIMPS Audit
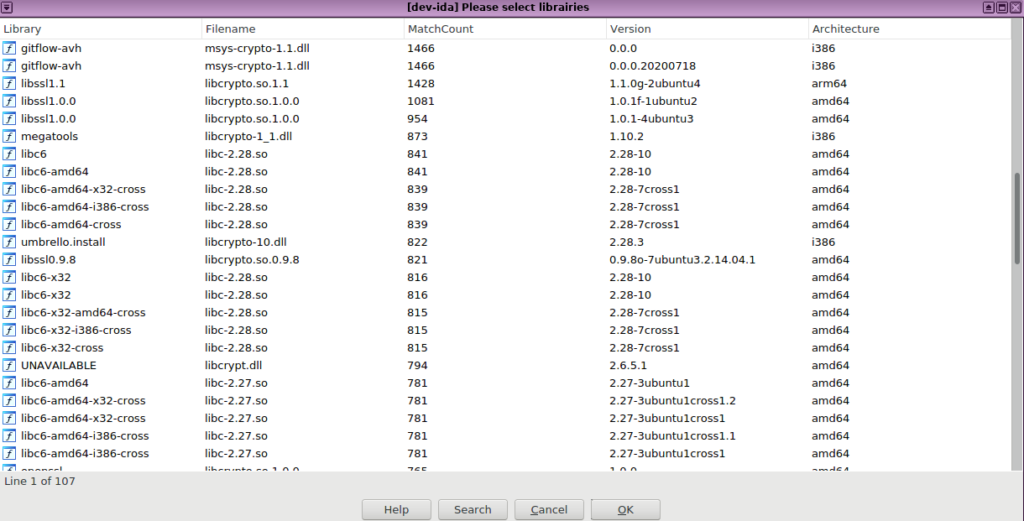
The GLIMPS Audit solution identifies, in a few minutes, the static libraries present in the file and allows an instant documentation of the functions directly in the interface of IDA. This saves several weeks of tedious work thanks to a multi-architecture identification independent of the compilation chains.
All the code recognized by the solution will then be reported in IDA:
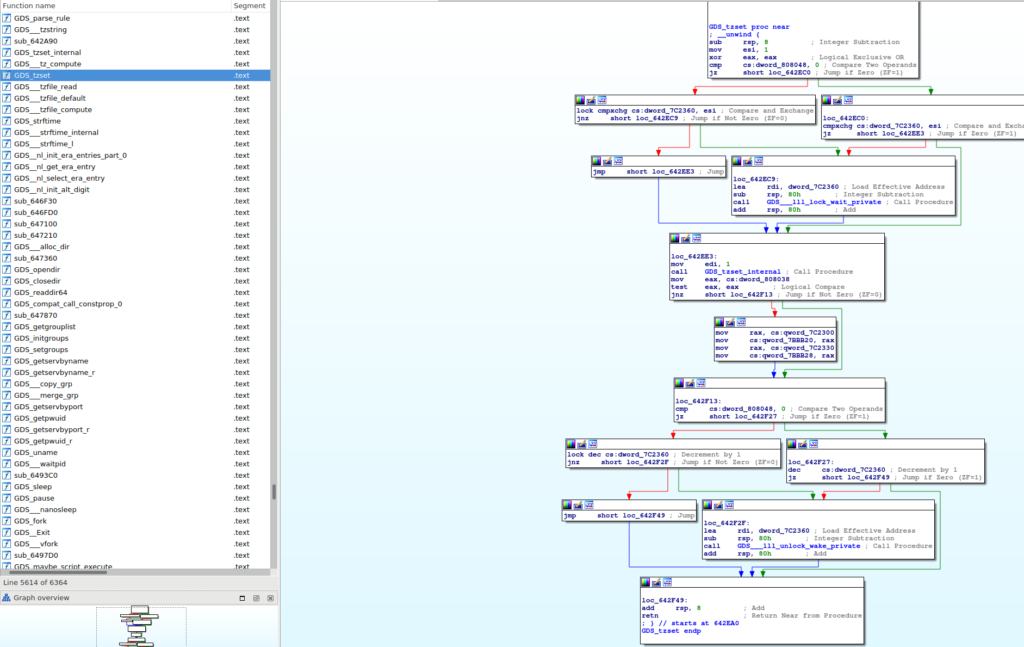
With the disassembled graph view, with automatically named functions on the left, it’s much easier for the analyst to understand the actions behind each function.
This plugin also allows you to build your own recognition datasets : upload the documentation you’ve done manually in the previous versions of a sample, and recover it when you get a new and different sample !
This even works in cross-architecture (x86 vs ARM for example) and cross build (changing build options of the compiler), since the function recognition uses our Deep Learning algorithm that transform a binary code into what we, at GLIMPS, call a Concept Code. What is that you should ask… If I say “printf”, you immediately see what I’m talking about, right? That’s nothing else than a concept code! And that’s what we look for in the binary: concepts of codes like printf, memcpy, and so on, even if they have been compiled in an way we have not met before…