This week, GLIMPS’ CTI team had the opportunity to analyze a new ransomware: BlackSuit. Thanks to GLIMPS Malware’s datasets functionality we were able to highlight the correlation between BlackSuit & Royal (the latter being very present in recent weeks).
Building a dataset
By keeping abreast of current event, the CTI team was able to build up a dataset containing several strains of the Royal ransomware family. It serves as a reference for this family, and is continually updated as new strains appear.
Strain Analysis
1c849adcccad4643303297fb66bfe81c5536be39a87601d67664af1d14e02b9e
This file was identified by GLIMPS Malware as malicious.
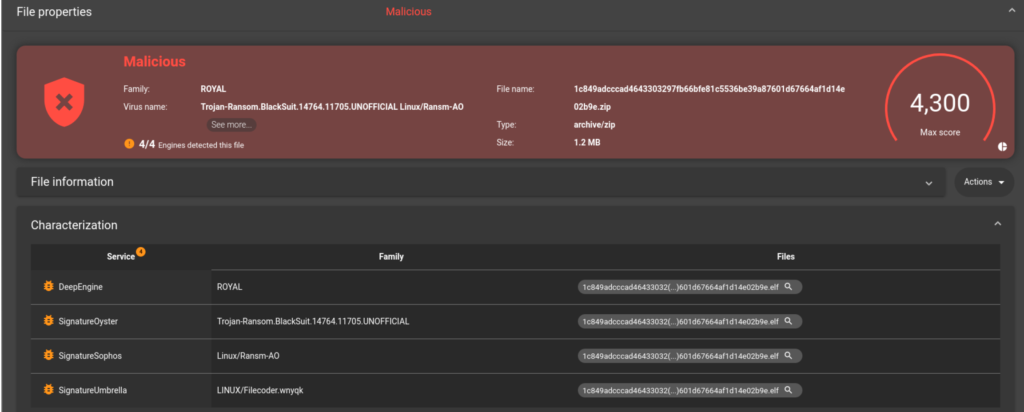
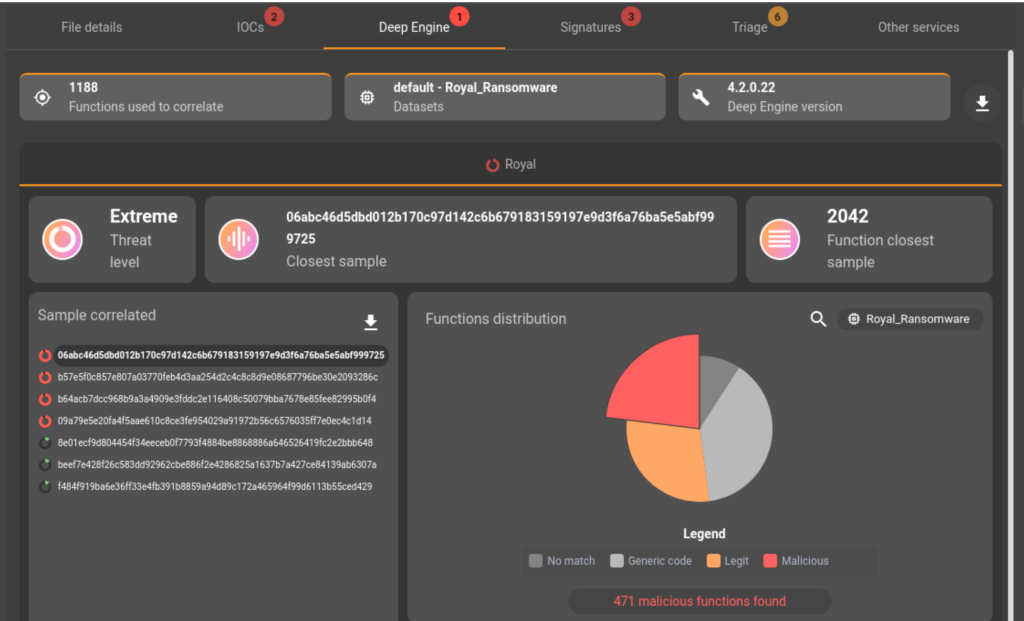
The deep engine analysis indicates that this sample includes functions used in binaries from the Royal family. .
This link between BlackSuit and Royal is highlighted by the GLIMPS Malware analysis platform.
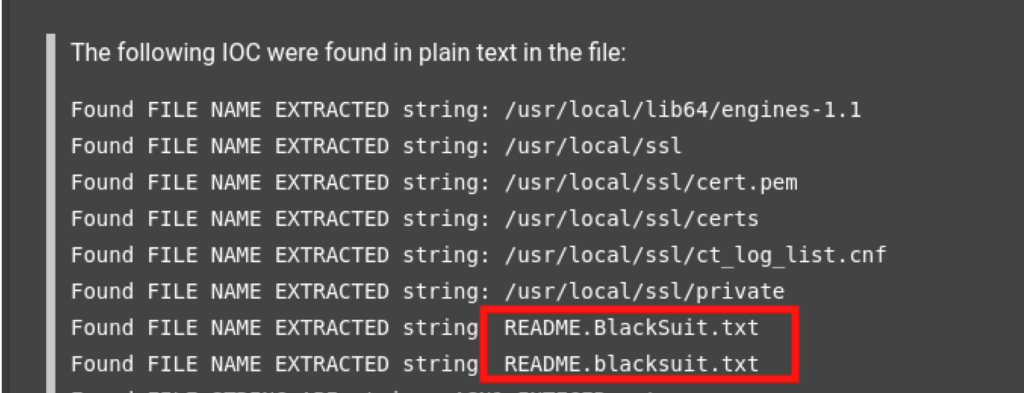
A study of strings shows that the ransom note is called README.BlackSuit.txt and that the link contained in it points to the attackers’ storefront belonging to BlackSuit.

Conclusion
It’s hard to say wHether this is a new family, but there are several possible explanations. Is it a source code leak ? Is it a conflict between the players ? Or is it simply a variant ? GLIMPS Malware has however, been able to show a link between these two families.
Appendices
| Hash | Description |
|---|---|
| 1c849adcccad4643303297fb66bfe81c5536be39a87601d67664af1d14e02b9e | Ransomware Elf file |
| IOC | Description |
|---|---|
| README.BlackSuit.txt | Ransom note |
| http://lockbitaptc2iq4atewz2ise62q63wfktyrl4qtwuk5qax262kgtzjqd[.]onion | Ransom payment portal |
Do not hesitate to contact us for more information: contact@glimps.re