In the field of ransomware, Lockbit is a group that keeps evolving. Proof of this is the discovery of a new version of the Lockbit ransomware. This new variant seems to be based on the source code of another well-known ransomware: Conti.
The Conti ransomware appeared in 2020 and quickly became a pioneer in the field. With the establishment of a very lucrative business model, the group gained popularity very quickly. One of their most famous victims is the HSE (Irish Health Service) in May 2021.
In 2021, an affiliate leaked internal documents to the team and created the first scandal surrounding the group. In 2022, following the group’s stance in favor of Russia in the war between it and Ukraine, an internal conflict erupted and this time it is the full source code of the ransomware that was released online. The Lockbit group took advantage of this leak to recover the source code and integrate it into theirs. With Lockbit’s victim list still on the rise, this new wave may not lower the trend.
We were able to obtain some strains of this new variant and submit them to our GLIMPS Malware analysis platform. We present here the results of the automated analysis performed.
Analysis of a first strain
45c317200e27e5c5692c59d06768ca2e7eeb446d6d495084f414d0f261f75315
This file is identified by GLIMPS Malware as malicious. The Deep Engine1 tells us that this sample embeds functions used in binaries of the Conti family as well as Lockbit. This link between Lockbit and Conti brought to light by our analysis platform leads us to investigate further.
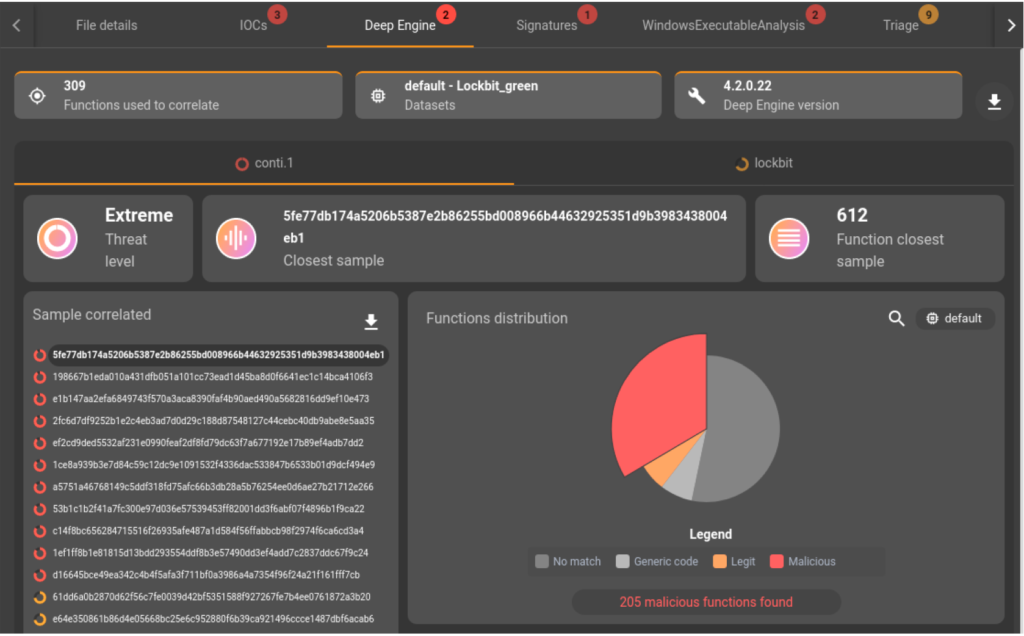
The strain is submitted for dynamic analysis via a sandbox connected to GLIMPS Malware and confirms that we are dealing with a ransomware without providing more information about the family at this stage.
Analysis of a second strain
fb49b940570cfd241dea27ae768ac420e863d9f26c5d64f0d10aea4dd0bf0ce3
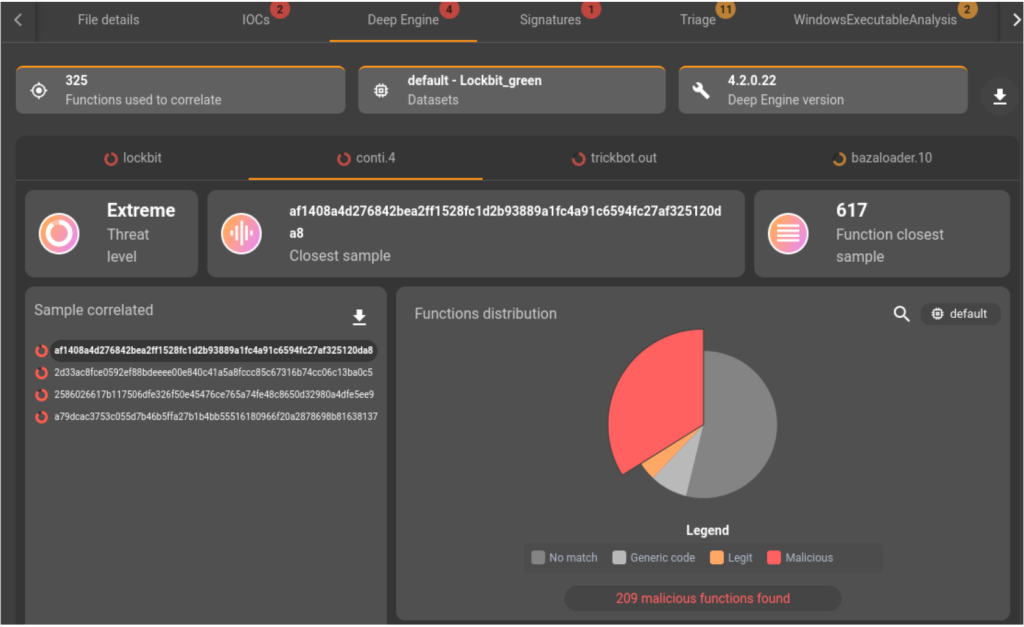
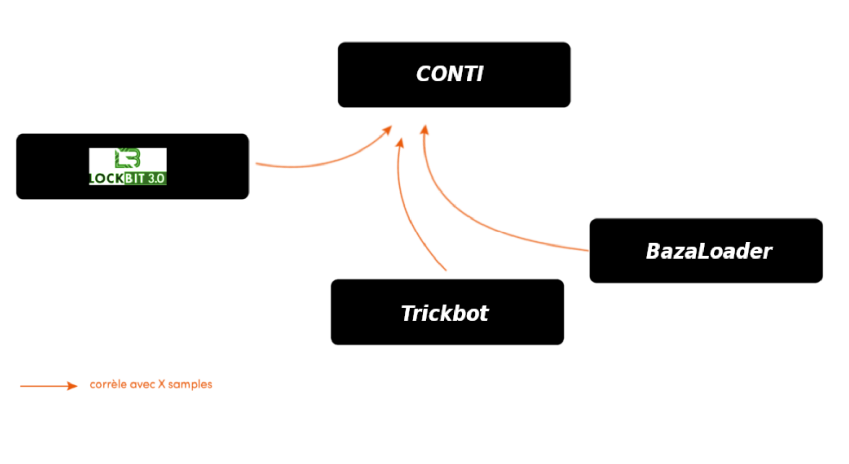
A second file, associated with the same campaign as the previous one, is analyzed. Like the previous sample, the Deep Engine found similarities with the Conti and Lockbit families as well as correlations with the Trickbot and Bazaloader families.
Trickbot elements are used by the Conti group in their attacks which explains the link found here. For BazaLoader, it’s a bit more subtle: the BazaLoader group has indeed, like Lockbit, used the Conti code that leaked in 2022. The links that appear here show transitivity in the Lockbit Green –> Conti <– BazaLoader relationships.
Analysis of a third strain
924ec909e74a1d973d607e3ba1105a17e4337bd9a1c59ed5f9d3b4c25478fe11
A third file, related to the previously analyzed binaries campaign, is submitted to our analysis platform. As with the second sample, the Deep Engine technology shows similarities with the Conti, Lockbit, Bazaloader and Trickbot families. Once again, the correlation with these families is quite obvious from the link mentioned in the previous analysis.
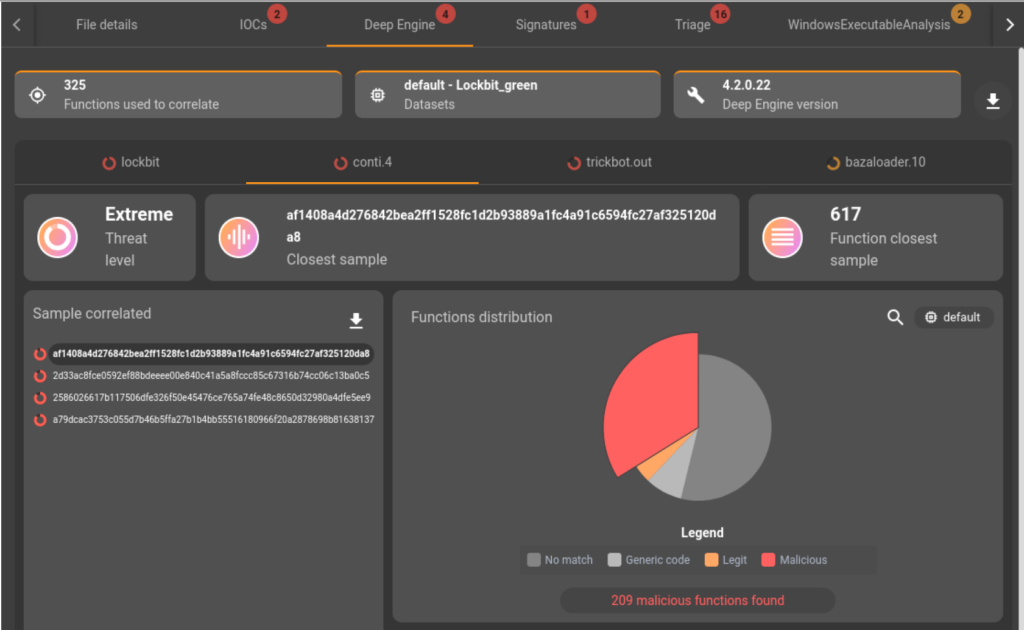
Moreover, following the detection of Lockbit families and thanks to our partnership with the CTI expert company Sekoia.IO., we can integrate the analysis report related to this group. This report also allows us to confirm the code link between the Lockbit and Conti families.
This time, the platform extracts a file whose iOCs are .onions links.
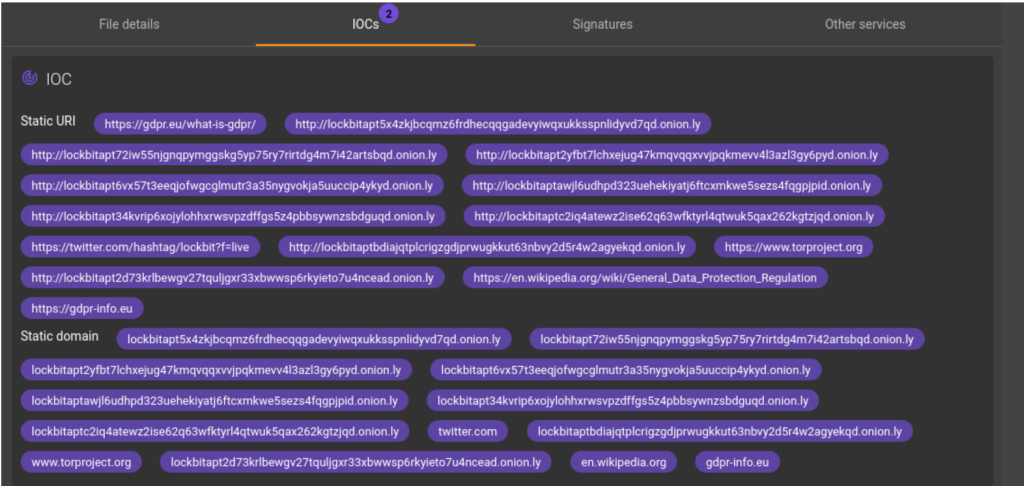
These links, which start with a Lockbit string, suggest that this would be the group’s ransomware payment portal. In order to deepen our analysis and wring out this malware, the file is submitted to dynamic analysis, which allows us to recover the ransom note of the ransomware. It seems that we are indeed facing one, or even several, Lockbit variants.
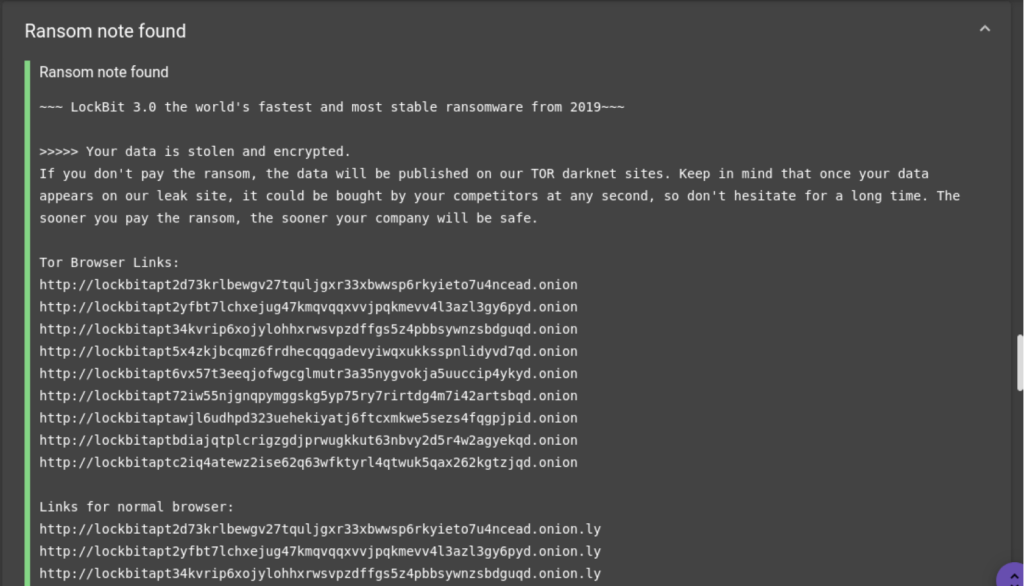
The sandbox analysis also highlights the change in file extension with a random string.

Unlike the previous versions, the extension of the files encrypted by Lockbit is no longer “.lockbit” but a random string of characters. The structure of the ransom note is the same as for Lockbit V3 (Lockbit Black).
Conclusion
The various results produced by the analyses combined with the information from CTI confirm what we thought at first. We are indeed facing Lockbit variants that shamelessly rely on Conti code, the Lockbit Green version.
Appendices
| Hash | Description |
|---|---|
| 45c317200e27e5c5692c59d06768ca2e7eeb446d6d495084f414d0f261f75315 |
Ransomware Exe file |
| fb49b940570cfd241dea27ae768ac420e863d9f26c5d64f0d10aea4dd0bf0ce3 |
Ransomware Exe file |
| 924ec909e74a1d973d607e3ba1105a17e4337bd9a1c59ed5f9d3b4c25478fe11 |
Ransomware Exe file |
| IOC | Descriptif |
|---|---|
| !!!-Restore-My-Files-!!!.txt |
Ransom note |
| http://lockbitapt2d73krlbewgv27tquljgxr33xbwwsp6rkyieto7u4ncead[.]onion | |
| http://lockbitapt2yfbt7lchxejug47kmqvqqxvvjpqkmevv4l3azl3gy6pyd[.]onion | |
| http://lockbitapt34kvrip6xojylohhxrwsvpzdff gs5z4pbbsywnzsbdguqd[.]onion | |
| http://lockbitapt5x4zkjbcqmz6frdhecqqgadevyiwqxukksspnlidyvd7qd[.]onion | |
| http://lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd[.]onion | |
| http://lockbitapt72iw55njgnqpymggskg5yp75ry7rirtdg4m7i42artsbqd[.]onion | |
| http://lockbitaptawjl6udhpd323uehekiyatj6ftcxmkwe5sezs4fqgpjpid[.]onion | |
| http://lockbitaptbdiajqtplcrigzgdjprwugkkut63nbvy2d5r4w2agyekqd[.]onion | |
| http://lockbitaptc2iq4atewz2ise62q63wfktyrl4qtwuk5qax262kgtzjqd[.]onion |
Ransom payment portal |
| http://lockbitsupa7e3b4pkn4mgkgojrl5iqgx24clbzc4xm7i6jeetsia3qd[.]onion | |
| http://lockbitsupdwon76nzykzblcplixwts4n4zoecugz2bxabtapqvmzqqd[.]onion | |
| http://lockbitsupn2h6be2cnqpvncyhj4rgmnwn44633hnzzmtxdvjoqlp7yd[.]onion | |
| http://lockbitsupo7vv5vcl3jxpsdviopwvasljqcstym6efhh6oze7c6xjad[.]onion | |
| http://lockbitsupq3g62dni2f36snrdb4n5qzqvovbtkt5xff w3draxk6gwqd[.]onion | |
| http://lockbitsupqfyacidr6upt6nhhyipujvaablubuevxj6xy3frthvr3yd[.]onion | |
| http://lockbitsupt7nr3fa6e7xyb73lk6bw6rcneqhoyblniiabj4uwvzapqd[.]onion | |
| http://lockbitsupuhswh4izvoucoxsbnotkmgq6durg7kfi cg6u33zfvq3oyd[.]onion | |
| http://lockbitsupxcjntihbmat4rrh7ktowips2qzywh6zer5r3xafhviyhqd[.]onion |
communication chat |
| fb7c204e |
encryption extension |
1. The Deep Engine is the deep learning engine developed by GLIMPS, which allows to compare and correlate computer codes. It is used at the heart of the GLIMPS Malware platform to enable the detection of malware, even when the codes have been modified by the attackers.
Do not hesitate to contact us for more information: contact@glimps.re